Le guide de l’authentification multifacteur (MFA)

Profitez d'un support IT efficace
Découvrez notre solution tout-en-un
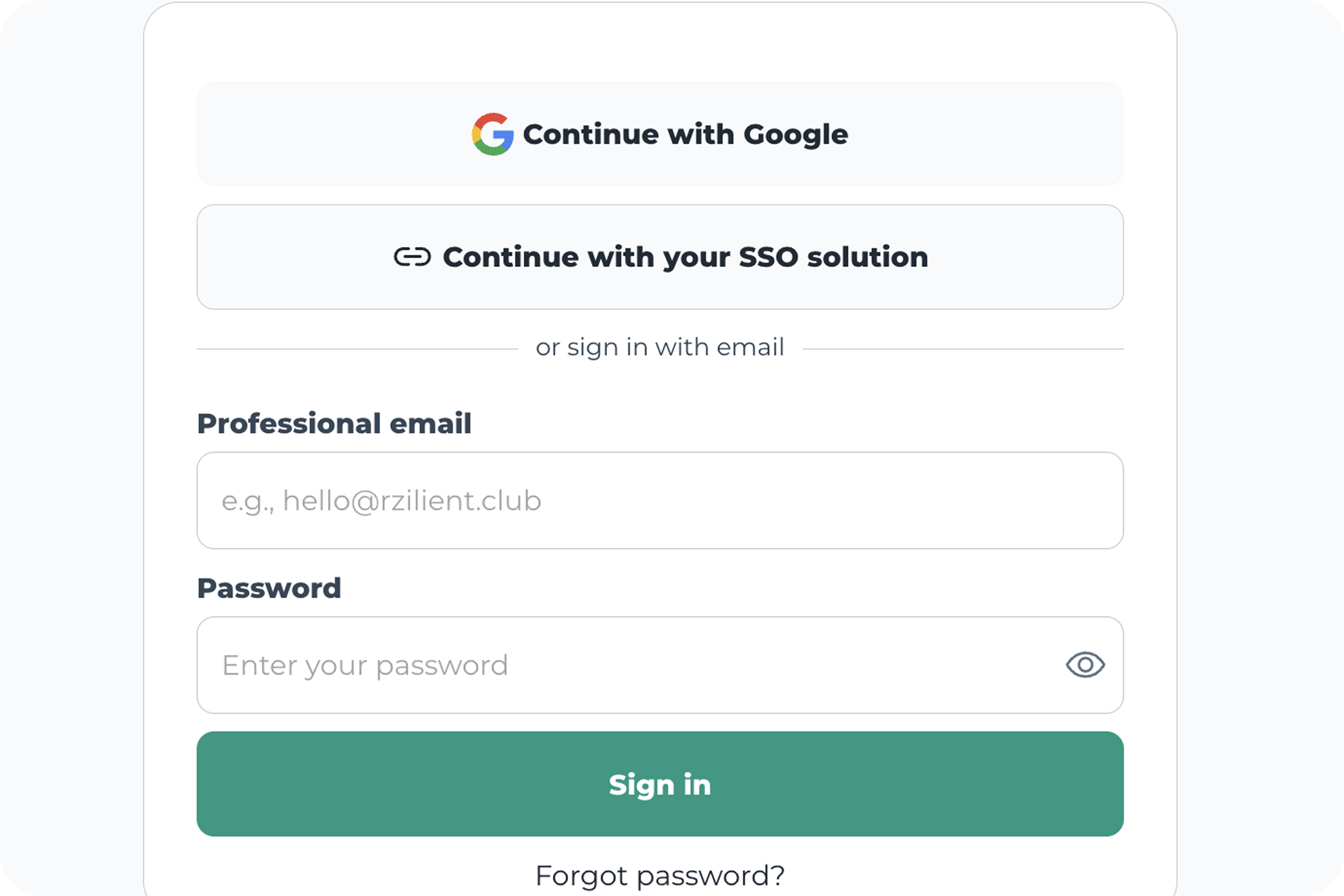
Imaginez que la porte d’entrée de votre entreprise ne se verrouille qu’avec un simple loquet. Facile à forcer, non ? C’est un peu la même chose avec un mot de passe unique. L’authentification multifacteur, ou MFA, ajoute plusieurs serrures à cette porte numérique.
En clair, la MFA est une méthode qui demande plusieurs preuves de votre identité avant de vous laisser accéder à un compte ou à une application. Ce n’est plus juste « mot de passe accepté », mais plutôt « prouvez-moi que vous êtes bien vous » — via un code reçu sur votre téléphone, votre empreinte digitale ou une clé physique par exemple.
Les différents types de facteur d’authentification
Quand on parle de MFA, on parle de panacher trois types de facteurs pour sécuriser l’accès à un système :
1. Facteurs de connaissances
Quelque chose que vous (et uniquement vous) savez :
- Un mot de passe
- Une question secrète (souvent oubliée… soyons honnêtes)
2. Facteurs de possession
Quelque chose que vous possédez :
- Un smartphone avec une app comme Google Authenticator
- Une clé de sécurité (type YubiKey)
- Un badge physique
3. Facteurs d’inhérence
Quelque chose que vous êtes :
- Empreinte digitale
- Reconnaissance faciale ou vocale

Pourquoi la MFA est-elle essentielle pour la sécurité ?
Les cyberattaques, tentatives d’hameçonnage et autres vols d’identifiants sont devenus monnaie courante. Et pourtant, plus de 80 % des violations de sécurité sont dues à un mot de passe faible ou compromis.
Avec la MFA, même si un attaquant a votre mot de passe, il lui faudra encore franchir une ou deux étapes supplémentaires pour accéder à vos données. Autant dire que ça refroidit beaucoup de tentatives.
Et au-delà de la technique, c’est un message fort : votre organisation prend au sérieux la sécurité des données et la protection de l’identité de ses collaborateurs.
Comment fonctionne l’authentification multifacteur ?
Voici comment ça se passe, en toute simplicité :
- L’utilisateur entre son identifiant + mot de passe.
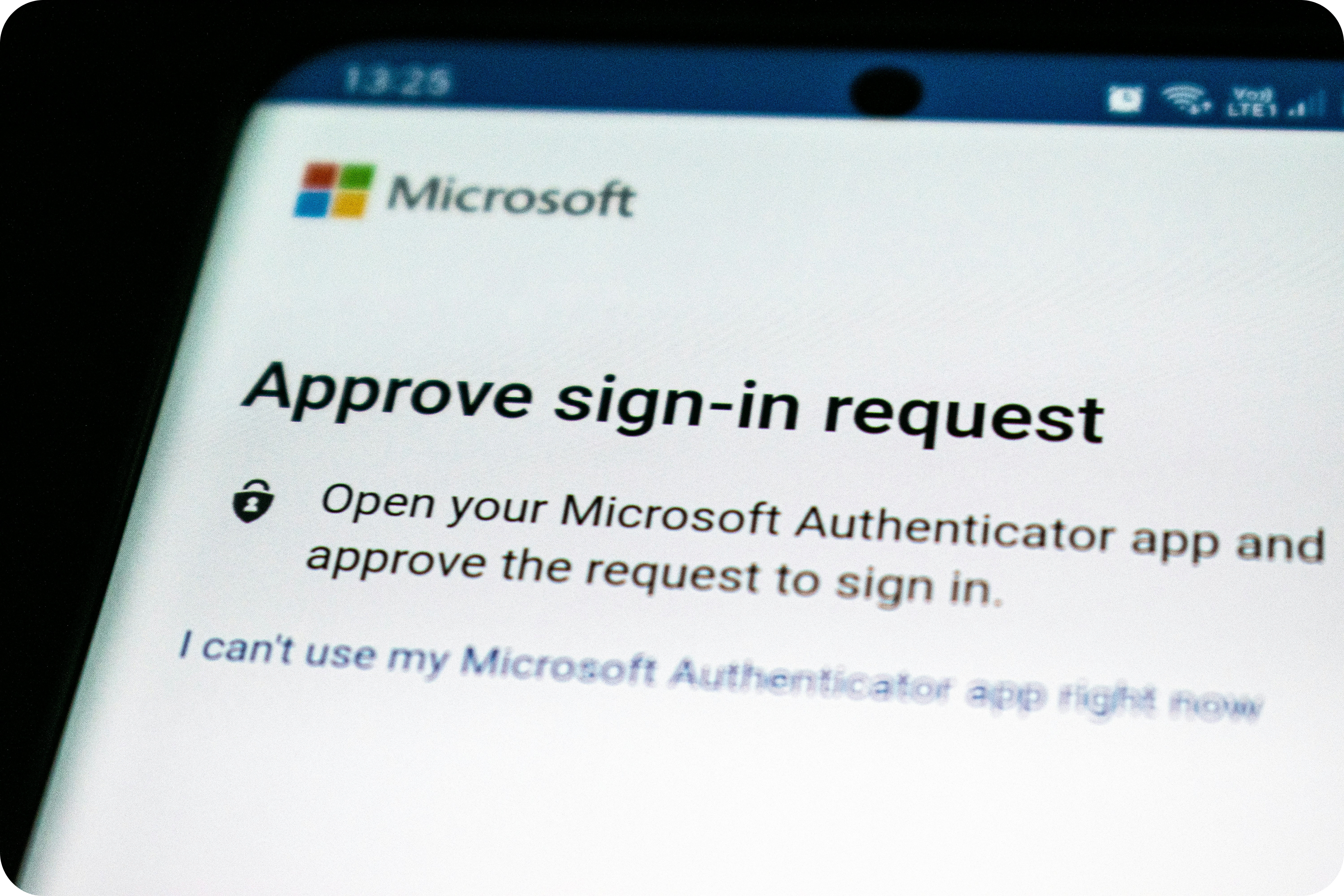
- Il reçoit un code temporaire (TOTP) ou une notification sur son téléphone.
- Il valide l’accès via son appareil ou une application dédiée.
Certaines solutions comme Microsoft Authenticator vont plus loin en proposant des connexions sans mot de passe. Résultat : moins de frictions, plus de sécurité.

Les avantages de l’implémentation de la MFA dans votre entreprise
On pourrait lister tous les bienfaits de la MFA dans un rapport de 30 pages, mais voici les principaux :
- Renforcement de la sécurité des comptes utilisateurs, que ce soit sur le cloud ou en local.
- Conformité avec les normes comme le RGPD ou l’ISO 27001.
- Réduction significative des attaques par hameçonnage ou usurpation.
- Augmentation de la confiance en interne comme en externe.
Pour les équipes IT et RH, la MFA devient un outil stratégique : elle protège l’identité numérique de chaque collaborateur tout en renforçant la posture globale de cybersécurité.
Les défis à prévoir lors de l’implémentation d’une solution MFA
On ne va pas se mentir, la MFA n’est pas un bouton magique. Voici les principaux obstacles rencontrés :
- Résistance au changement : certains utilisateurs peuvent percevoir ça comme une contrainte.
- Contraintes techniques : tous les outils ou postes de travail ne sont pas toujours compatibles.
- Cas particuliers : comment gérer les prestataires externes, les invités, ou les postes partagés ?
Astuce rzilient : Prévoir une communication claire, des guides utilisateurs simples, et du support au déploiement fait toute la différence.







