Gestion centralisée des identités & habilitations
Une solution de gestion des identités et des accès qui fait gagner du temps à vos équipes, compatible avec vos applications SaaS, Hybrides ou On-premise.
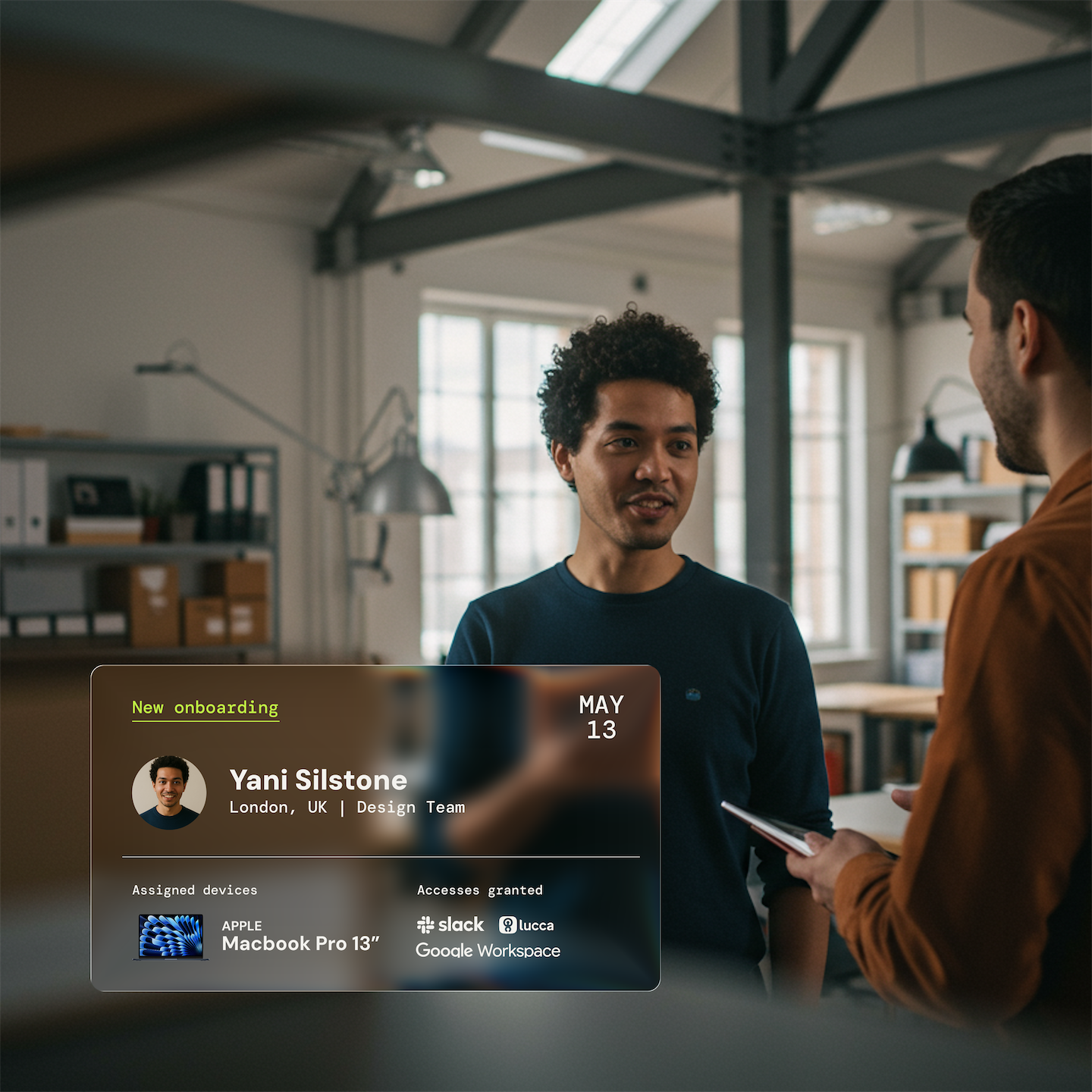
Identifiez les utilisateurs clés
Identifiez et catégorisez les utilisateurs essentiels de votre système, leur attribuant des rôles et des permissions précis.
Assurez-vous que chaque utilisateur ait accès uniquement aux ressources nécessaires à son rôle, garantissant ainsi la sécurité et la confidentialité des données sensibles.
Sécurisation des données
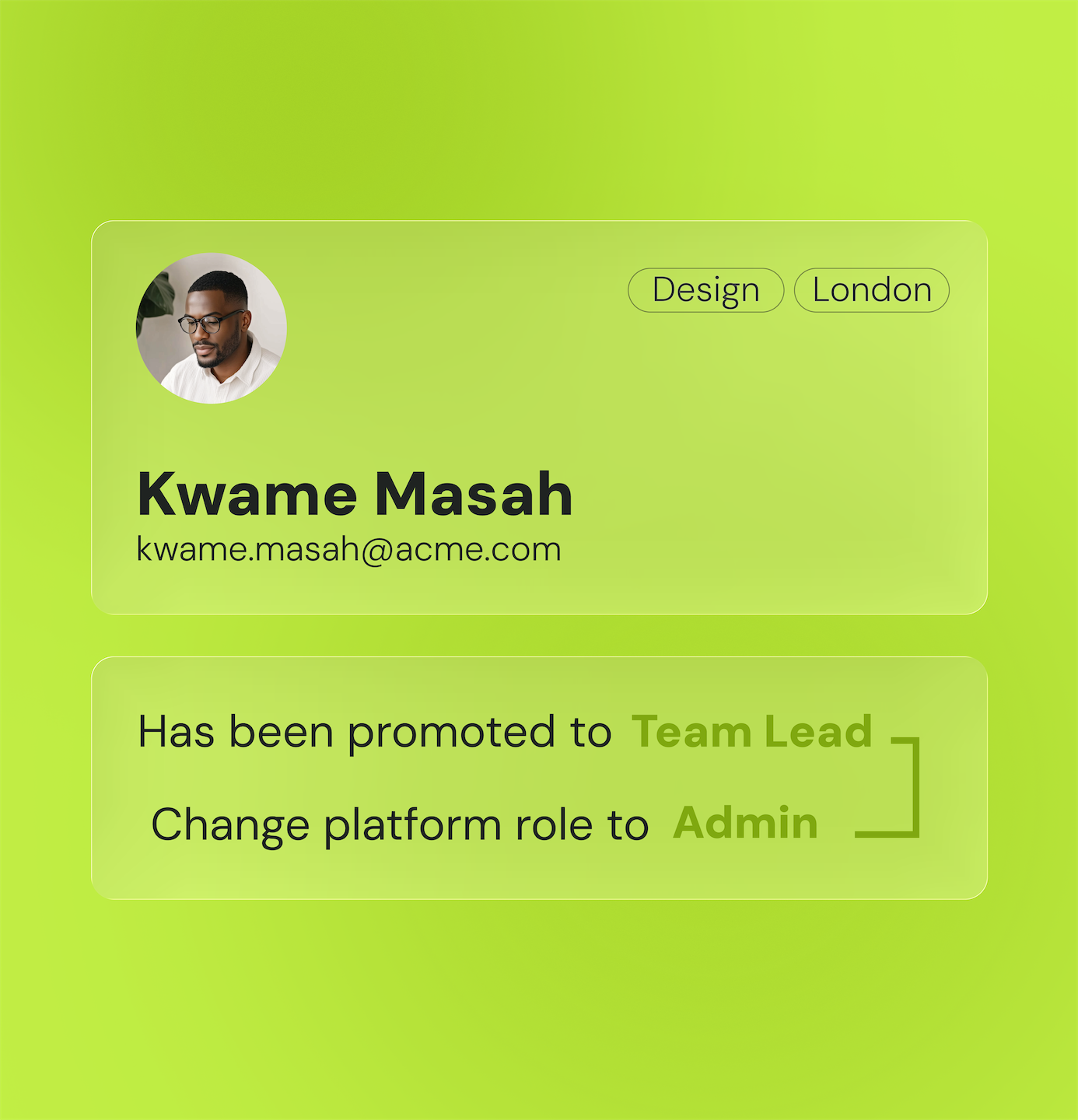
Simplifiez la gestion des accès
Simplifiez la gestion des droits d'accès en automatisant les processus de demande, d'approbation et de révocation des autorisations.
Réduisez les risques liés aux erreurs humaines en mettant en place des workflows intelligents et des règles de gouvernance strictes pour chaque type d'accès.
Contrôle à distance
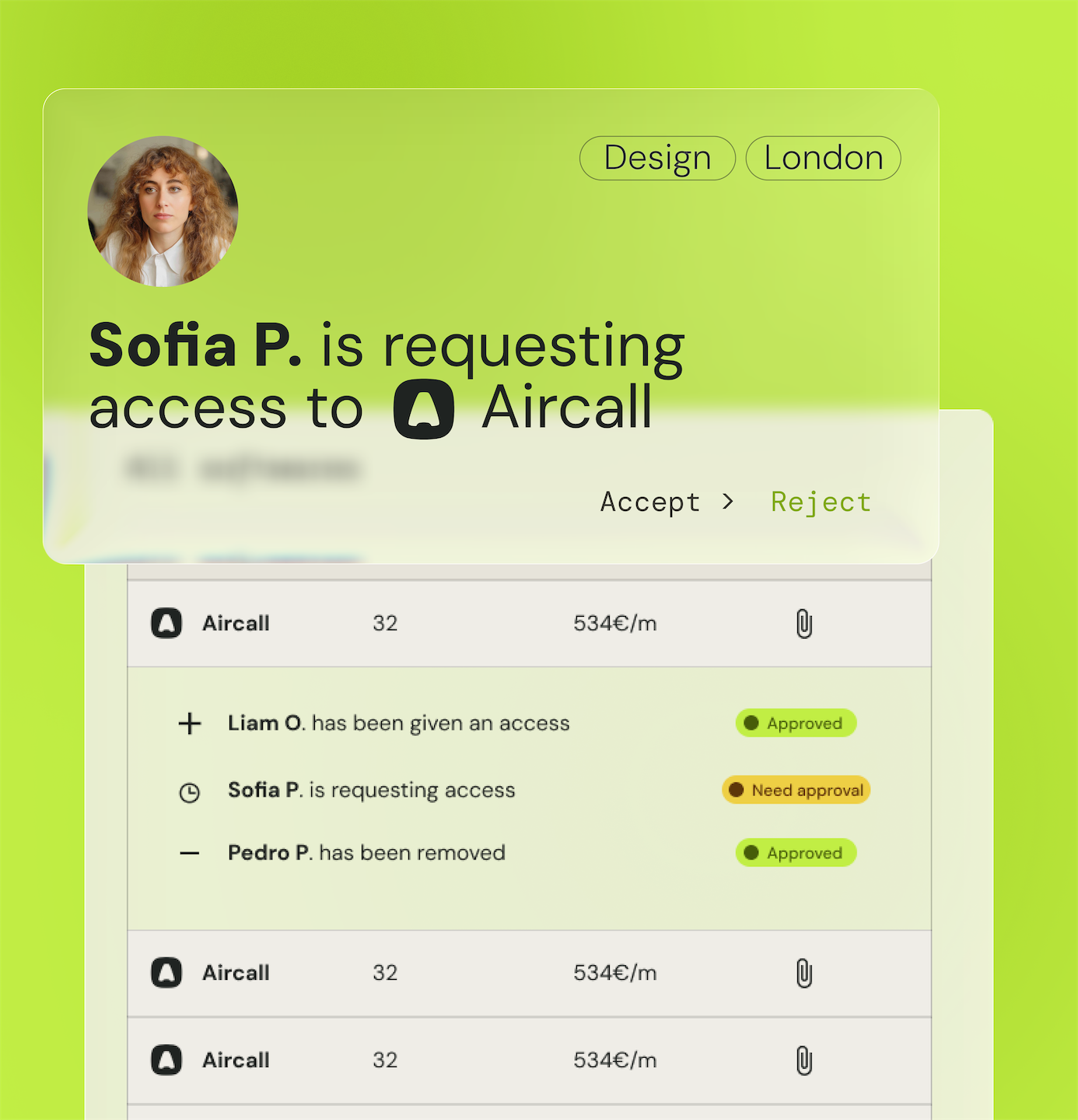
Renforcez la sécurité des données
Protégez vos informations sensibles en mettant en œuvre des mécanismes d'authentification multi-facteurs (MFA) et des stratégies de chiffrement robustes.
Surveillez en temps réel les activités des utilisateurs pour détecter et répondre rapidement aux comportements suspects ou aux tentatives d'accès non autorisées.
Détection proactive
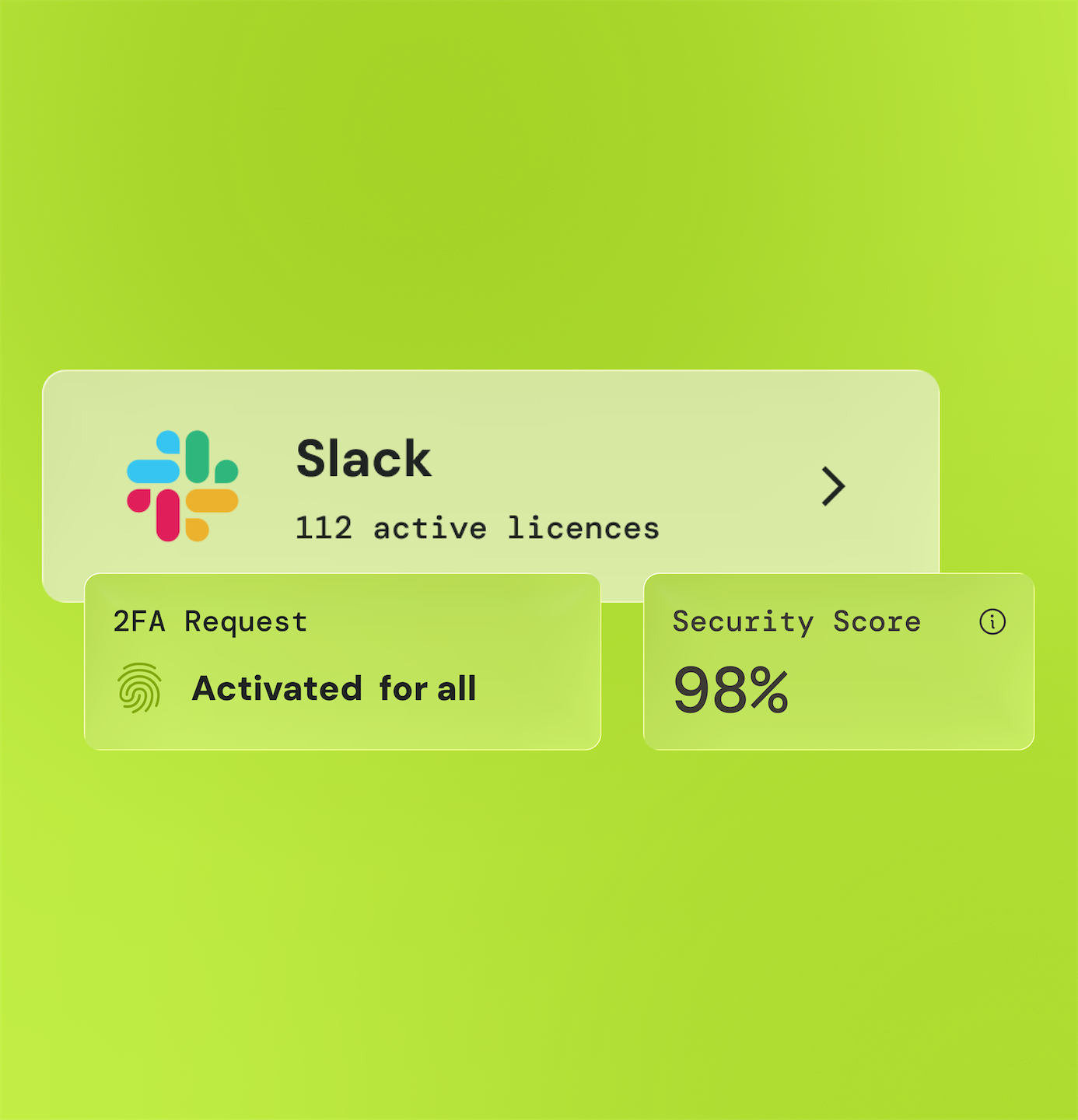
Garantissez le respect des politiques
Restez en conformité avec les réglementations et les normes de sécurité en vigueur en automatisant les processus de génération de rapports et d'audit.
Garantissez la traçabilité des actions des utilisateurs pour répondre aux exigences de conformité et éviter les amendes et les sanctions potentielles.
Mise en conformité

Contrôlez vos accès en toute sécurité
FAQs
Retrouvez nos réponses à vos questions les plus fréquentes. Encore des doutes ? Échangez avec l'un de nos experts !
Nous veillons à ce que chaque utilisateur accède uniquement aux ressources essentielles à son rôle, garantissant la sécurité et la confidentialité des données sensibles. Cela est réalisé par une attribution minutieuse des rôles et des permissions qui correspondent strictement aux nécessités opérationnelles de l'utilisateur.
Notre solution automatise les processus de demande, d'approbation, et de révocation des autorisations. Cela simplifie considérablement la gestion des droits d'accès tout en réduisant les erreurs humaines et en augmentant l'efficacité opérationnelle.
Tout votre parc IT, en un seul outil
Simplifiez votre gestion informatique avec une plateforme SaaS intuitive et toutes les fonctionnalités dont vous avez besoin.
MDM
Identités & Habilitations
On/Offboardings
Inventaire
SaaS management