Comprendre le SSO et ses enjeux pour votre entreprise

Profitez d'un support IT efficace
Découvrez notre solution tout-en-un
Vous en avez assez de jongler entre 10 mots de passe par jour, d’oublier celui de l’app RH ou de vous reconnecter à HubSpot après chaque pause café ? Rassurez-vous, vous n’êtes pas seul·e. C’est justement pour répondre à cette fatigue digitale que le SSO (Single Sign-On) a vu le jour. Dans cet article, on vous explique simplement ce que c’est, pourquoi c’est utile pour vos équipes IT et RH, et surtout, comment le mettre en place sans se perdre dans le jargon technique.
Qu’est-ce que le SSO ?
Définition du SSO
Le Single Sign-On (SSO) est une méthode d’authentification permettant à un utilisateur de se connecter une seule fois pour accéder à un ensemble d’applications ou de services web. Plutôt que de mémoriser plusieurs identifiants et mots de passe, l’utilisateur entre ses informations une seule fois via un fournisseur d'identité central qui gère les accès. Cela simplifie la vie des collaborateurs tout en renforçant la sécurité informatique.
Comment fonctionne l’authentification SSO ?
L’authentification SSO repose sur un dialogue entre trois acteurs :
- L’utilisateur
- Le fournisseur d'identité (IdP)
- Le fournisseur de services (SP)
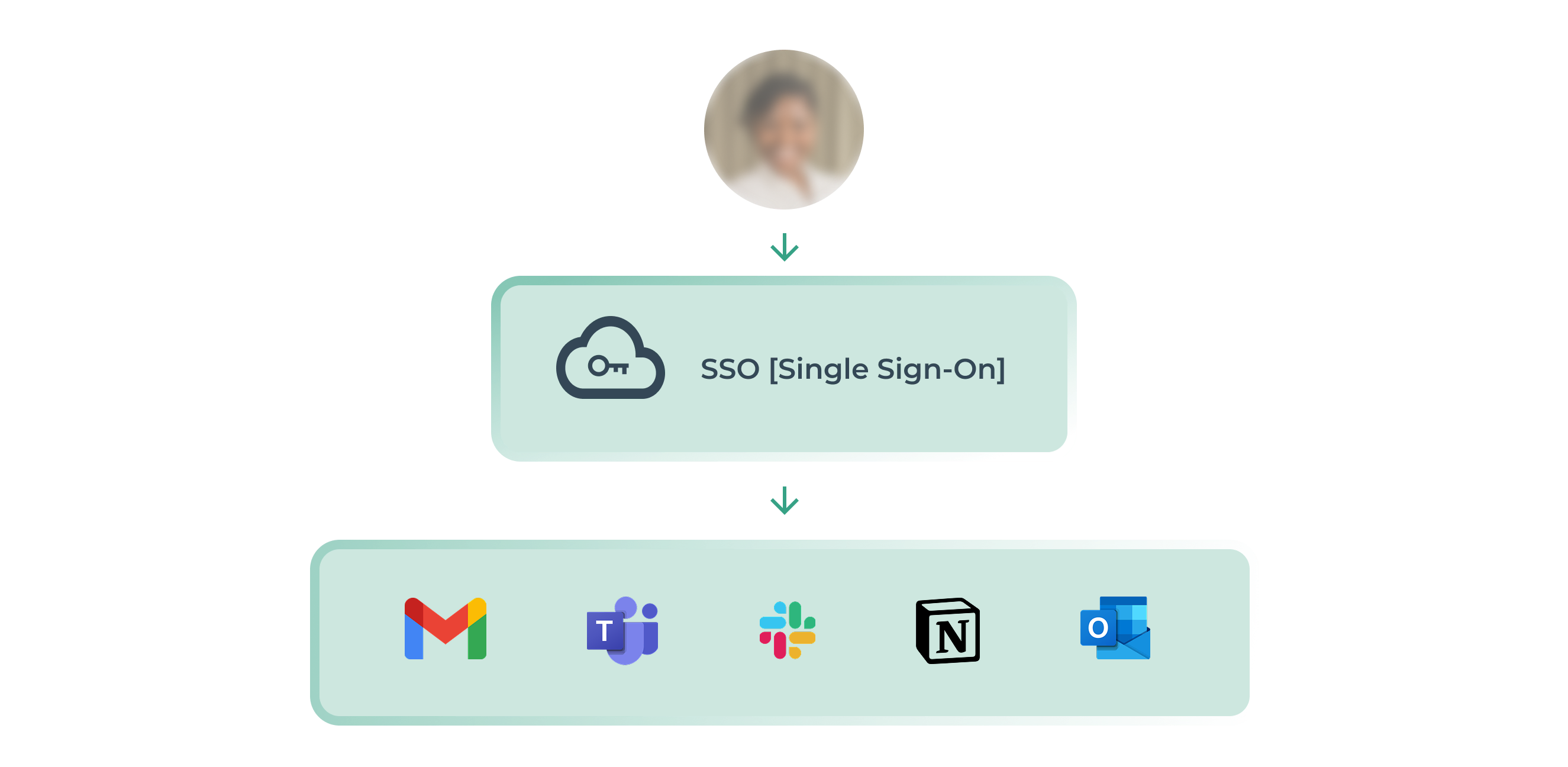
Concrètement :
- Vous cliquez sur l'URL d'une application (HubSpot par exemple).
- Vous êtes redirigé vers votre fournisseur d'identité (comme Google).
- Vous vous connectez une fois.
- Un jeton d'authentification est envoyé pour vérifier votre identité.
- Vous accédez aux autres services sans ressaisir vos identifiant
Les avantages de l’intégration du SSO dans votre entreprise
Les gains sont concrets, à la fois pour les équipes techniques et les collaborateurs :
- Moins de mots de passe à retenir, donc moins d’oublis et moins de frictions.
- Moins de tickets pour le support IT, souvent engorgés par les demandes de réinitialisation.
- Expérience employé améliorée, notamment pour les onboarding.
- Plus de sécurité, avec une authentification centralisée, plus facile à contrôler.
- Moins de shadow IT : les apps validées sont accessibles plus facilement.
Bref, c’est un petit changement qui peut transformer la manière dont vos équipes utilisent leurs outils au quotidien.
Mettre en oeuvre le SSO dans votre entreprise
Les différents types de SSO
SAML (Security Assertion Markup Language)
Le vétéran du SSO. Idéal pour les apps d’entreprise comme Google Workspace ou Salesforce.
OAuth (Open Authorization)
Moins pour s’authentifier que pour donner un accès partiel à des données à une autre application. Typiquement utilisé sur les API ou pour se connecter via un compte Google ou Facebook.
OpenID Connect (OIDC)
La version moderne et sécurisée d’OAuth. Parfaite pour les apps web et mobiles.
Kerberos
Un classique des réseaux Windows. Moins utilisé dans les environnements cloud.
Les critères à prendre en compte dans votre choix de solution SSO
Avant de se lancer, quelques questions à se poser :
- Vos outils (HubSpot, Notion, Slack...) sont-ils compatibles ?
- Quelle est la politique de sécurité de votre entreprise ?
- Souhaitez-vous garder le contrôle sur l’identité en interne ou passer par un tiers ?
- Qui va gérer les connexions ? Votre équipe IT, un prestataire, ou la plateforme rzilient ?
Intégration et déploiement du SSO
Voici à quoi ressemble un déploiement SSO réussi :
- Audit de vos applications et besoins : pour identifier les priorités.
- Choix du fournisseur d'identité : Google, Azure AD, Okta...
- Configuration : échange de certificats, métadonnées, URLs...
- Tests : ne rien laisser au hasard.
- Formation des équipes et support en cas de souci.
Avec la plateforme rzilient, on vous accompagne dans chaque étape pour garantir une intégration fluide, sans perturber votre activité.

Comparaison du SSO avec d’autres solutions d’accès
Gestion des identités fédérées
Le principe : on fait confiance à un tiers pour valider une identité (ex : un partenaire B2B). On est dans une logique inter-entreprises.
Same sign-on
Pas de connexion unique ici. Juste les mêmes identifiants synchronisés entre plusieurs applications. Moins pratique, plus rigide.
Authentification multi-facteurs (MFA)
Le MFA ajoute une étape à votre login : un SMS, une appli de validation, une empreinte digitale... C’est souvent utilisé en complément du SSO pour plus de sécurité.
Le SSO, ce n’est pas un luxe : c’est un vrai réflexe de sécurité et d’efficacité, surtout pour les PME et scale-up qui gèrent de plus en plus d’outils en ligne. C’est aussi une façon concrète d’améliorer la vie de vos équipes, tout en gardant la main sur ce qui compte : les accès, les données, les identités.







