Les cyberattaques les plus courantes en entreprise

Profitez d'un support IT efficace
Découvrez notre solution tout-en-un
Phishing, ransomwares, DDoS… Les cyberattaques ne cessent de se multiplier. Mais concrètement, quelles sont les attaques informatiques les plus fréquentes, et comment s’en prémunir efficacement ? On vous explique tout dans cet article clair et sans jargon, avec des exemples concrets.
Pourquoi les entreprises sont ciblées par des cyberattaques ?
Que vous soyez une startup, une PME ou une grande organisation, vous êtes une cible. Pourquoi ? Parce que les entreprises, quel que soit leur secteur, manipulent des données sensibles, utilisent de nombreux systèmes informatiques et collaborent avec des utilisateurs variés (employés, partenaires, prestataires).
Plus encore, la transformation numérique accélère l’exposition aux risques : travail à distance, applications web, outils SaaS… Cela multiplie les portes d’entrée pour les cybercriminels.
Les cyberattaques les plus fréquentes en entreprise
On distingue plusieurs types de cyberattaques. Voici les plus courantes et comment elles fonctionnent.
Le Phishing (hameçonnage) et ses variantes
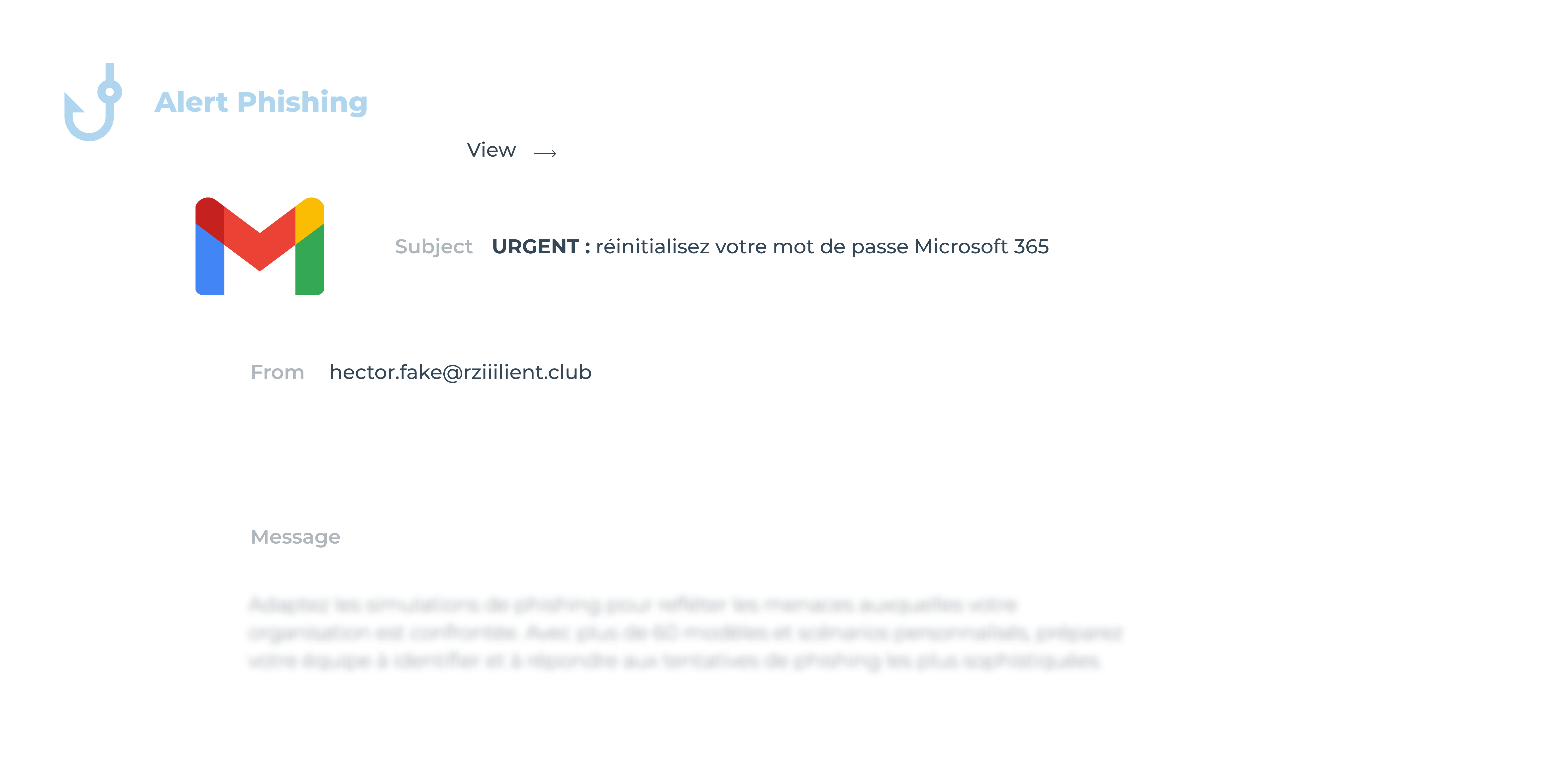
C’est la porte d’entrée préférée des hackers. Un email qui semble provenir d’un collègue ou d’un service client, une pièce jointe piégée, un lien vers une fausse page de connexion… et l’utilisateur se fait avoir.
👉 Mise en situation : Un employé reçoit un email “urgent” pour réinitialiser son mot de passe Microsoft 365. Il clique, entre ses identifiants… et donne les clés de l’entreprise au pirate.
Les ransomwares (rançongiciels)
Ces logiciels bloquent vos données et exigent une rançon pour les débloquer. Ils se propagent souvent via une pièce jointe malveillante ou une faille non corrigée.
En 2023, plus de 70 % des attaques ransomware visaient des entreprises françaises. Le plus dangereux ? Une fois touché, il est souvent trop tard.
Les malwares (logiciels malveillants) et virus
Ces logiciels peuvent espionner, voler ou détruire des informations. Certains restent invisibles pendant des mois, récoltant des données confidentielles sans que personne ne s’en rende compte.
Les attaques par déni de service distribué (DDoS)
L’idée ici : saturer vos serveurs avec des millions de requêtes pour bloquer votre site ou vos services. C’est fréquent contre les sites e-commerce, les plateformes SaaS ou les services publics.
Les attaques par ingénierie sociale
Pas besoin de technologie : ici, l’humain est la faille. Appels frauduleux, usurpation d’identité, manipulation psychologique… L’attaquant exploite la confiance ou la panique.
👉 Mise en situation : Un “technicien IT” appelle pour demander un mot de passe à un collaborateur. Ce dernier, croyant bien faire, le transmet.
Les menaces internes
Parfois, le danger vient de l’intérieur : un employé mécontent, un stagiaire mal informé, ou tout simplement une erreur humaine.
Comment protéger son entreprise contre les cyberattaques ?
Face à ces menaces, la bonne nouvelle, c’est qu’il existe des solutions simples et accessibles pour se protéger.
Sensibilisation et formation des employés
C’est la première ligne de défense. Vos collaborateurs doivent savoir reconnaître une tentative de phishing, éviter les mots de passe faibles, et signaler les comportements suspects.
💡 Une courte formation ou des rappels réguliers peuvent réduire les risques de plus de 70 %.

Mise en place de politiques de sécurité informatique
Définissez des règles claires : gestion des accès, utilisation des appareils personnels, authentification forte, etc.
Utilisation de logiciels et pare-feu de sécurité
Antivirus, pare-feu, outils de surveillance, systèmes de détection d’intrusion… Autant d’outils indispensables pour protéger vos systèmes et données.
Mise à jour régulière des systèmes et logiciels
Les failles de sécurité sont souvent corrigées par des mises à jour… à condition qu’elles soient appliquées. Ne les repoussez pas !
Sauvegarde et récupération des données
Même avec toutes les précautions du monde, le risque zéro n’existe pas. Une sauvegarde régulière de vos données vous permettra de reprendre votre activité rapidement en cas d’attaque.
Besoin d’un accompagnement expert ? Découvrez la cybersécurité managée par _rzilient
Pour les entreprises qui veulent aller plus loin sans mobiliser une équipe IT en interne, _rzilient propose une offre de cybersécurité managée.
Concrètement, cela signifie que nous supervisons, sécurisons et mettons à jour votre système informatique au quotidien, avec des solutions adaptées à votre structure. Du monitoring à la gestion des incidents, en passant par les audits de sécurité, vous êtes protégé en continu.
Une solution clé en main, conçue pour les PME, qui vous fait gagner du temps… et de la tranquillité.

En résumé
Les cyberattaques sont nombreuses, mais elles ne doivent pas paralyser votre activité. Avec les bons réflexes, les bons outils et un peu de vigilance, vous pouvez fortement limiter les risques.
Et si vous ne savez pas par où commencer ? Chez _rzilient, on vous accompagne avec des solutions sur mesure pour protéger votre système informatique, vos données et vos équipes.







