Les normes de cybersécurité : quelles démarches suivre ?

Profitez d'un support IT efficace
Découvrez notre solution tout-en-un
ISO27001, SOC2, DORA… les normes et labels de cybersécurité existent depuis maintenant plusieurs décennies, mais restent encore un mystère pour beaucoup.
Quelles sont ces normes dont tout le monde parle ? Que veulent-elles dire ? Comment se différencient-elles ?
On vous explique tout dans cette article.
Les fondements des normes en cybersécurité
Qu’est-ce qu’une norme en cybersécurité ?
La cybersécurité est un monde obscure, qui paraît presque impossible à dompter.
Alors, dans le but d’éclairer le chemin et d’attester du bien-faire des organisations suivant rigoureusement ces règles essentielles à la sécurisation des environnements numériques et à la protection des utilisateurs, des organismes mondiaux et régionaux ont créer des labels, aussi appelés normes.
Ces normes en cybersécurité sont comme une feuille de route. Elles définissent les meilleures pratiques pour sécuriser vos systèmes d’information, protéger vos données, et prévenir les risques.
En bref : une norme, c’est une garantie que votre organisation suit un cadre structuré et fiable.
Les organismes de normalisation
Comme nous l’évoquions, elles sont développées par des organismes spécialisés, reconnus internationalement, pour guider les organisations face aux menaces grandissantes.
Derrière ces normes, on trouve des acteurs majeurs comme l’ISO (Organisation internationale de normalisation) ou la Commission électrotechnique internationale (IEC). Ils établissent des standards mondialement reconnus.
D'autres organismes, tels que le NIST (National Institute of Standards and Technology) aux États-Unis, ou des initiatives régionales comme l’ANSSI en France, complètent ces cadres pour répondre à des besoins spécifiques.
Chaque norme est le fruit d’un consensus d’experts : chercheurs, professionnels, et décideurs.
Les objectifs des normes de cybersécurité
Pourquoi suivre une norme ? Les objectifs sont multiples :
• Intégrité, confidentialité et disponibilité des informations.
• Réduction des risques de cybersécurité.
• Conformité avec les réglementations en vigueur, comme le RGPD ou la directive NIS2.
• Renforcement de la confiance des parties prenantes.
Ces objectifs convergent vers un seul but : garantir la résilience de votre organisation dans un environnement incertain.
Présentation détaillée des principales normes de cybersécurité
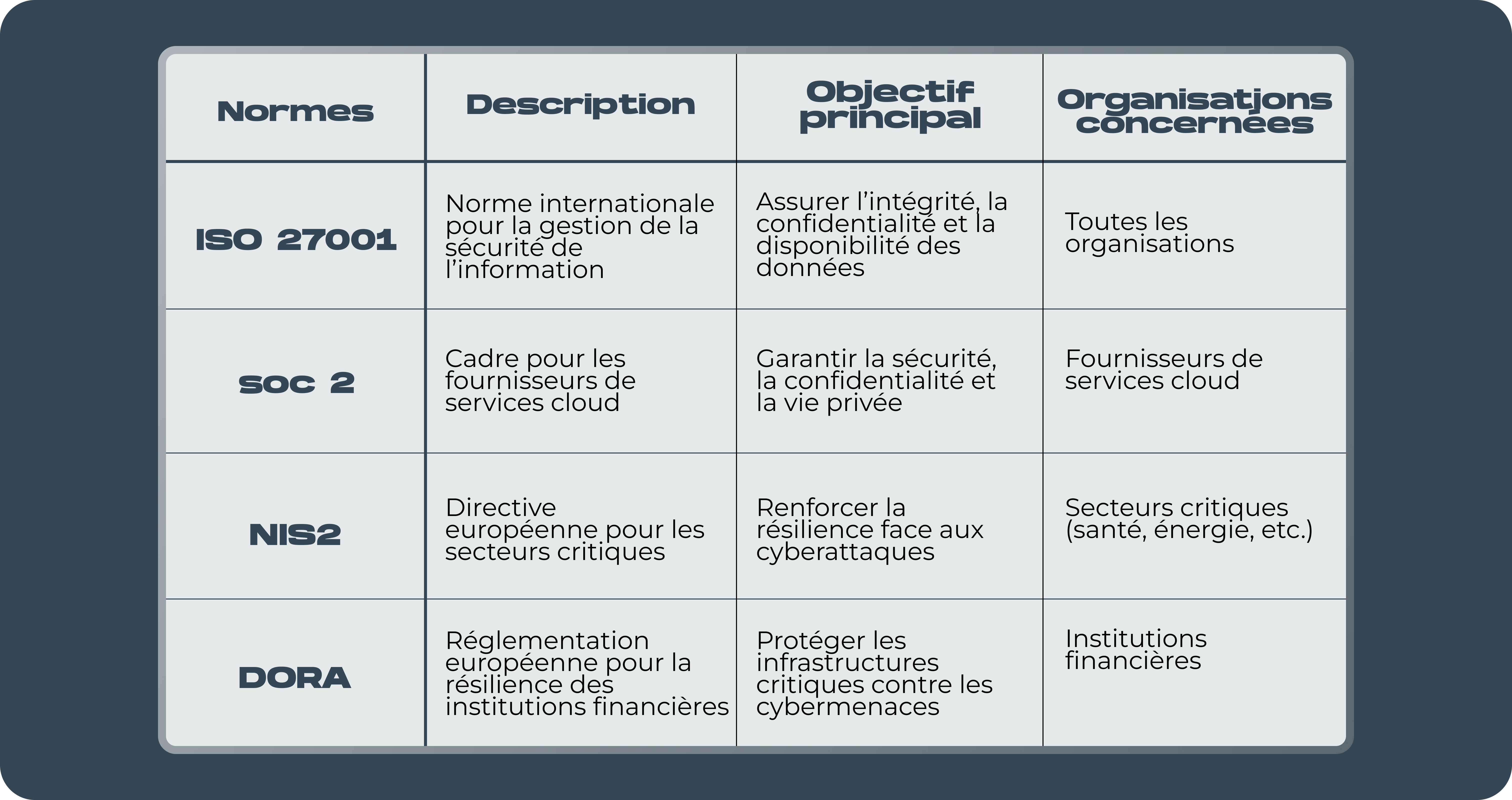
ISO 27001
L’ISO 27001 reste la norme incontournable lorsqu’il s’agit de la gestion de la sécurité de l’information. Reconnue mondialement, elle établit les exigences pour la mise en place d’un Système de Management de la Sécurité de l’Information (SMSI). L’objectif est de garantir l’intégrité, la confidentialité et la disponibilité des informations critiques pour votre organisation.
L’ISO 27001 repose sur une approche basée sur la gestion des risques, permettant d’identifier et de traiter les menaces spécifiques à votre environnement. De plus, elle s’adapte à des organisations de toutes tailles et secteurs, ce qui en fait une solution universelle.
👉 Découvrez notre guide sur ISO 27001.
Rzilient vous accompagner pour vous conformer à cette norme, comme ce fût le cas avec Boondmanager ou MobilityWork.
SOC 2
Conçu pour les fournisseurs de services cloud, SOC 2 est basé sur cinq critères de confiance :
- Sécurité,
- Disponibilité,
- Intégrité du traitement,
- Confidentialité,
- Vie privée.
SOC 2 est particulièrement pertinent pour les entreprises SaaS ou celles qui traitent de grandes quantités de données sensibles pour leurs clients. La certification prouve que votre organisation suit des processus rigoureux pour protéger les données, renforçant ainsi la confiance des parties prenantes.
Nuances entre SOC 2 Type I et Type II :
- Type I : Évalue si les contrôles sont correctement conçus à un moment donné. Idéal pour une certification rapide.
- Type II : Examine l’efficacité des contrôles sur une période prolongée (6 à 12 mois), offrant une validation approfondie et continue.
NIS2
La directive NIS2 (Network and Information Security Directive) est une évolution de la directive NIS originale, adoptée par l’Union européenne. Elle cible les secteurs critiques, comme les télécommunications, la santé ou l’énergie, en imposant des mesures de cybersécurité strictes pour prévenir et répondre aux cyberattaques.
Parmi ses principales exigences :
• Mise en place de politiques robustes de gestion des risques.
• Collaboration accrue entre les États membres en cas d’incidents.
• Renforcement de la transparence et des obligations de reporting.
Cette directive est essentielle pour toute organisation opérant dans l’UE, et rzilient offre un accompagnement personnalisé pour s’y conformer.
DORA
La réglementation DORA (Digital Operational Resilience Act), également émise par l’Union européenne, vise à renforcer la résilience opérationnelle numérique des organisations financières. À l’ère des cyberattaques sophistiquées, cette réglementation exige que les institutions financières mettent en place des mesures robustes pour protéger leurs infrastructures critiques.
Les exigences incluent :
• Des audits réguliers de la cybersécurité.
• Une gestion stricte des risques liés aux fournisseurs tiers.
• Une réponse rapide et efficace aux incidents.
DORA est un atout majeur pour les entreprises cherchant à renforcer leur posture de cybersécurité dans le secteur financier.
Avantages des normes de cybersécurité
Adopter une norme, c’est bien plus qu’une démarche administrative. Voici ce que cela peut apporter à votre organisation :
1. Une gestion des risques renforcée
Les normes de cybersécurité vous aident à anticiper et à gérer les risques avant qu’ils ne deviennent des problèmes majeurs. En suivant des cadres comme l’ISO 27001 ou SOC 2, vous identifiez vos vulnérabilités, évaluez leur impact potentiel et mettez en place des mesures pour les limiter. Cela réduit non seulement les chances d’une cyberattaque réussie, mais aussi les coûts liés à une violation des données.
2. Confiance accrue auprès de vos clients et partenaires
Les entreprises certifiées démontrent leur engagement en matière de sécurité. Cela rassure vos clients, partenaires et investisseurs, qui savent que leurs informations sont entre de bonnes mains. C’est un véritable avantage concurrentiel, notamment dans les secteurs sensibles comme la finance, la santé ou le commerce en ligne.
Et sans oublier !
Certaines normes, comme SOC 2, sont souvent exigées par des clients grands comptes. Être certifié peut ouvrir la porte à de nouvelles opportunités commerciales.
3. Conformité légale simplifiée
Entre le RGPD, les directives NIS2 et les réglementations sectorielles comme DORA, il est facile de se sentir dépassé. Les normes de cybersécurité vous permettent de cocher plusieurs cases à la fois en intégrant les exigences réglementaires dans votre stratégie. Cela évite les sanctions coûteuses et les complications juridiques.
Un exemple concret ? La conformité à NIS2, qui impose des mesures de gestion des risques et des audits réguliers, peut être facilitée grâce à l’adoption d’une norme comme ISO 27001.
4. Amélioration de l’efficacité opérationnelle
Les normes ne se contentent pas de renforcer la sécurité. Elles favorisent aussi une meilleure organisation interne. En définissant des processus clairs pour la gestion des incidents, la formation des employés ou encore la maintenance des systèmes, elles permettent de gagner du temps et d’optimiser les ressources.
Résultat : Vos équipes travaillent avec plus de sérénité et moins de pertes de temps liées à des procédures floues ou inefficaces.
5. Une résilience accrue face aux cyberattaques
Adopter des normes de cybersécurité, c’est investir dans la résilience de votre organisation. Cela signifie que même en cas d’incident, vous avez les outils, les processus et les ressources pour réagir rapidement et limiter les dégâts.
Point important : La résilience n’est pas seulement technique. Les normes incluent souvent des éléments liés à la communication de crise, essentiels pour protéger votre réputation en cas d’incident majeur.
6. Une culture de la sécurité au sein de l’organisation
Les certifications ne sont pas qu’un enjeu technique. Elles encouragent une prise de conscience collective des enjeux de cybersécurité, du stagiaire au CEO. Cette culture de la sécurité devient un levier stratégique pour mobiliser les équipes et responsabiliser chacun dans ses pratiques.
Exemple : Un employé formé à la sécurité sera plus attentif aux tentatives de phishing ou à l’utilisation d’appareils non sécurisés.
Les normes de cybersécurité évoluent
Le paysage des cybermenaces ne cesse de changer. Les normes, elles aussi, évoluent pour répondre aux défis modernes : nouveaux types d’attaques, explosion des données, et émergence des technologies comme l’IA.
À ce titre, les standards se penchent désormais davantage sur :
• La gestion des risques liés à l’intelligence artificielle.
• L’adoption de mesures spécifiques au télétravail.
• La collaboration mondiale pour faire face aux cyberattaques transfrontalières.
rzilient peut vous accompagner vers une certification en cybersécurité
Se lancer dans une démarche de certification peut sembler intimidant. Par où commencer ? Quelles étapes prioriser ? Chez rzilient, nous simplifions ce processus pour vous.
Nous vous accompagnons à chaque étape :
- Évaluation de votre système existant.
- Définition des mesures nécessaires pour atteindre la conformité.
- Mise en place et suivi des bonnes pratiques.
Avec notre expertise, vous n’êtes jamais seul·e dans ce voyage vers un environnement numérique plus sûr.
Prêts à passer à l’action ? Contactez-nous dès aujourd’hui et transformez vos défis en opportunités !






